Cryptography methods of protection in programming languages
Victor Rudometov
The main problems and ways of their solution
In process of transition from an epoch of an industrial civilisation to mainly informational the role stored and appropriate amount of the handled knowledge considerably increases. Appearance and prompt development of computer networks has provided effective ways of data transfer and fast access to the information both for separate people, and for the big organisations. However local and global computer networks, however, as well as other ways of an information transfer, can represent threat for safety of data, especially in the absence of adequate measures of their protection against unauthorized access.
Thus, now, in process of formation of an informational society of a protection frame become one of the main tools. They provide confidentiality, privacy, confidence, authorisation, electronic payments, corporate safety and uncountable set of other important attributes of a modern life.
In this connection presence of the built in mechanisms of protection of the information and efficiency of their operation in application systems even more often gains defining value at a choice consumers of optimal solution. Therefore attention implementators of software for a long time already pay to the given questions. Cryptography methods can provide a due security clearance.
The mathematical cryptography has arisen as a science about enciphering — a science about cryptosystems. In classical model of system of confidential link there are two participants it is necessary for them to handle the confidential (confidential) information which has been not intended for the third parties. The given task about support of confidentiality, protection of the classified information against the external opponent, is one of the first tasks of cryptography.
There are some approaches to task in view solution.
First, it is possible to try to create data link absolutely reliable and unavailable to another. Unfortunately, to reach it it is the extremely difficult, at least, at existing level of modern development of a science and engineering which give methods and resources not only information transfers, but also unauthorized access to it.
The second approach is usage of readily available data links and concealment of the fact of transmission of any information. The science shorthand is engaged in the given direction. Unfortunately, shorthand methods cannot guarantee high level of confidentiality of the information.
The third way is to use a readily available data link, but to handle data in the transformed sort so restore them the target could only. Development of methods of conversion of the information providing its enciphering, also the cryptography is engaged.
In due course the cryptography usage has extended and has left far forwards from the initial purpose. By way of illustration this position it is possible to consider the following example. We will accept, the client of bank is intended to transfer money from the score on the score of any organisation. Here it is necessary to mark, what not the handled information is confidential. Really, it is necessary to transfer only bank accessories which are well-known and readily available. However it is important to bank to be convinced, that their owner, instead of the malefactor wishes to translate money. The client is interested in that the sum has not been changed, and nobody could transfer money from his name or change the information on the payee.
It is necessary to mark, that the cryptosystem works on certain methodology (procedure).
This methodology provides usage:
· one or more algorithms of enciphering which can be expressed in the form of mathematical formulas;
· the keys used by given algorithms of enciphering,
· management systems of keys,
· the non-encoded text,
· the ciphered text (shifrteksta).
The example of the circuit of methodology of enciphering with usage of keys is presented on fig. 1.
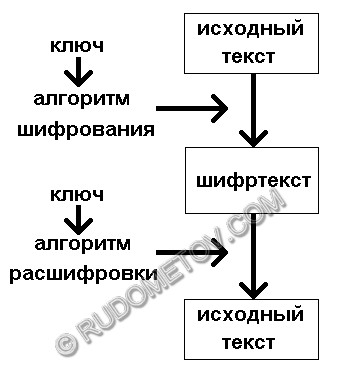
Fig. 1. An example of the circuit of enciphering.
Classification of cryptography algorithms
There are two methodologies with usage of keys: symmetric, providing private key application, and non-central — with an open key. Each methodology uses own procedures, ways of allocation of keys, their types and algorithms of enciphering and decryption.
In symmetric (symmetric) methodology with a private key one key with which help it is made both enciphering, and decryption by the same algorithm of symmetric enciphering uses. This key is handled two participants of interaction by safe image before transmission of the ciphered data. A problem is that fact that it is safe to extend private keys difficultly enough. It is possible to carry rather big high-speed performance to advantages of the given system at enciphering and decryption of handled messages.
Example of constant usage of symmetric methodology is the network of cash dispenses ATM. These systems are original developments of banks owning them and are not on sale.
In non-central (asymmetric) methodology with an open key two interconnected keys use. One of keys is stored in a secret, and another is published in open sources. The data ciphered by one key, can be decrypted only other key. One of the major lacks is a necessity of usage of very big keys on the size for safety support, that, undoubtedly, is mirrored in speed of operation of algorithms of enciphering.
Often both methodologies are combined. For example, the symmetric (confidential) key which is handled by means of algorithms of non-central methodology is generated.
It is possible to carry to widespread algorithms of symmetric methodology DES (Data Encryption Standard), 3-DES, RC2, RC4 and RC5. An example non-central are RSA and ECC. And the separate position is occupied with one of the most popular algorithms of digital signature DSA (Digital Signature Algorithm).
The urgency of a problem of saving of integrity or confidentiality of the information was obvious at all times. But especially sharply it has appeared with development of information technologies, in particular, a wide-area network the Internet. This network provides a convenient, operative way of link. Usage of special resources provides necessary levels of confidentiality. Thus in a modern life the user of the computer quite often should meet such most complicated algorithms, as RSA or DSA. As a result already almost for anybody does not call surprise possibility of usage of the digital signature or even enciphering of letters of e-mail E-mail (fig. 2).
Fig. 2. An example of possibility of usage of cryptography protection systems at information sending through the Internet
Presence of the built in mechanisms of protection of the information in application systems even more often gains defining value at a choice their consumers. Therefore attention implementators of software for a long time already pay to the given question.
Unfortunately, operation on creation and testing of cryptography protection demand essential financial expenses. The qualified employees, for example, kriptografy and programmers with hooshim mathematical derivation are besides, necessary. These factors substantially define quality of development and implementation of general-purpose interfaces by the large companies.
Many corporations including the largest system integrators, applying cryptography protection in the application systems, have gone on path of implementation of general-purpose interfaces. Their tasks include allocation to the application of a wide set of possibilities on call of cryptography tools. Such approach provides a system flexibility and its certain independence of algorithms. As a result of such approach software developers do not have necessity to think of what algorithms of cryptography protection will use in their product. Interfaces of calls of functions of the protection created by indirect manufacturers use only.
For example Sun Microsystems corporation offering to software developers language Java with a wide set of interfaces, realising the main cryptography algorithms and protocols can be.
Cryptography in Java
Considering language Java, it is necessary to remind, that this language is created rather recently and has as set of advantages, and it is a lot of lacks. Often advantages reduce to possibility of creation of machine-independent applications. However there are also others, probably, even more important in the conditions of prompt development of an informational society. It is a question, for example, of a network trend by language development. In 1993 company Sun has paid attention to growth of popularity of the Internet and has started to finish Java so that it was possible to start the written programs from Web-browsers (applets). Also language have been built in and the expanded possibilities of an application creation of type the client/server.
In connection with an obvious network trend of language Java it was required to pay due attention to protection frames. First of all it concerns transfers of the important data between the client and a server, and also activation of programs or applets. Such resources have been developed and built in a set of common libraries (JDK security API).
For example of necessity of protection the desire of the user-receiver to have possibility of verification that gives certain guarantees of authenticity of the document or a code can be. As the signed object the applets which widespread on the Internet can appear. As a result the receiver has a confidence, that the information is received from the expected remailer, instead of the possible malefactor, and has not been changed in the course of transfer. For support of such safety digital signatures and certificates are.
Algorithm DSA
The main idea of the digital signature (digital signature) consists in the following.
Let's accept, the remailer wishes to transmit to the receiver some data. He "signs" the document or a code by means of the special closed key (private key). This key is generated by means of the utility keytool or resources API. In this case "signs" means, that the special digital signature by means of the utility jarsigner or resources API is generated.
The diagramme illustrating passing through all stages of the signature of jar-archive (operation of the remailer), is presented on fig. 3. It is necessary to mark, that in a jar-file there can be any data, for example, the program, a picture or Word document.
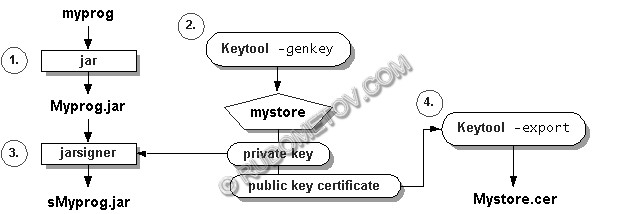
Fig. 3. Sequence of operations at the jar-archive signature.
The diagramme illustrating operation of the receiver of jar-archive, is presented on fig. 4.
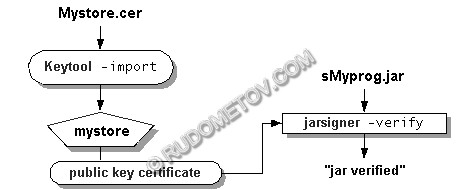
Fig. 4. Sequence of operations at verification of the received jar-archive.
In the course of generation of the closed key, there is also a so-called open key (public key) which "corresponds" to the closed.
To the receiver following data go:
1. A source document or a code,
2. The digital signature (or separately, or as a part of a jar-file),
3. An open key.
The receiver, having accepted all three components, by means of an open key defines authenticity of the signature and integrity of the document. Security of the given method consists that for a fake or breaking it is necessary to generate the closed key. Thus for the given task there is no "fast" algorithm provided that the length of keys is great enough.
But the specified simple method has the lacks and inaccuracies. The matter is that the receiver in the offered circuit certainly assumes authenticity and integrity of an open key. However the malefactor could change or change an open key, and, therefore, to generate the false signature and to change the document. Thus, the mechanism certifying authenticity of an open key is necessary.
For example certificates (certificate) can be. They are delivered by the indirect organisations and comprise an open key and some additional information. As the last the information on the remailer, data on the supplier of the certificate and the digital signature, giving a certain guarantee appears, that the open key belongs to the remailer.
In such situation if the confidence to the composer of the certificate takes place, it is possible to consider a problem solved. Otherwise it is necessary to access to one more indirect organisation and to request the new certificate certifying authenticity of already available certificate. And so on until the user not nejdet the organisation to which he can trust completely. Otherwise it is possible to try to use the self-signed certificates (CSR).
It is necessary to mark, that the proof of complexity of "breaking" of the given method needed enormous mathematical researches.
Let's consider possibility of usage Java Security for generation and verification of the digital signature.
Operation of the remailer
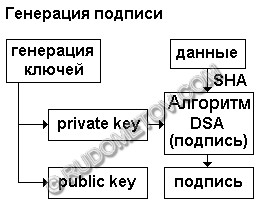
Fig. 5. The circuit of operations at signature generation
Generation of keys
The programmer, not penetrating into mathematical formulas and their features realizatsiii, can use already accessible ready algorithms and cryptography methods. They are given by the certain organisations, so-called providers (provider). By default built in resources Java are delivered by the provider "SUN". Thus, the only thing that it is necessary to do, it to specify purely algorithm and the provider.
First of all it is necessary to generate pair of keys - public key and private key. Class KeyPairGenerator For this purpose uses. For reception of the concrete object of this class it is necessary to call static factory a method getInstance (). As arguments strings with algorithm and provider instructions are handled. For example, for usage DSA (Digital Signature Algorithm) and provider SUN it is necessary to write:
KeyPairGenerator keyGen = KeyPairGenerator.getInstance ("DSA", "SUN");
Because the majority of cryptography algorithms are probability, it is necessary to create a probability source — the object of class SecureRandom. Thus there is a possibility to use different methods, for example, SHA1PRNG (pseudo-random-number generation algorithm).
SecureRandom random = SecureRandom.getInstance ("SHA1PRNG", "SUN");
Now it is necessary to initialize keyGen object, having handled it of 2 parametres — length bits and a randomness source.
keyGen.initialize (1024, random);
The last stage is purely generation of pair keys (a method generateKeyPair ()) and selection of two separate keys (methods getPrivate () and getPublic ()).
KeyPair pair = keyGen.generateKeyPair ();
PrivateKey privKey = pair.getPrivate ();
PublicKey pubKey = pair.getPublic ();
Signature creation.
First of all it is necessary to create the object of class Signature, having called a method getInstance ():
Signature dsa = Signature.getInstance ("SHA1withDSA", "SUN");
In this case algorithm DSA with SHA1 (hashing function) uses. Then there is a process of initialization of the signature by a key. At this stage the closed key received earlier uses:
dsa.initSign (privKey);
After that it is necessary to reduce the signature and data. The method update (), a byte data array received as parametre which should be signed is for this purpose called.
At the last stage the signature which is represented in the form of the byte array is generated.
byte [] realSig = dsa.sign ();
Signature saving.
After reception of the signature and keys it is necessary to save them, for example, in a file and to send to a target together with input data. It is necessary to underline, that the closed key is not dispatched, and remains for the remailer. The open key is referred.
So, the remailer dispatches to the receiver, for example, by e-mail or through direct network interconnection following files:
1. An open key (public key)
2. The digital signature (digital signature)
3. Input data (the signed document or a code).
Operation of the receiver.
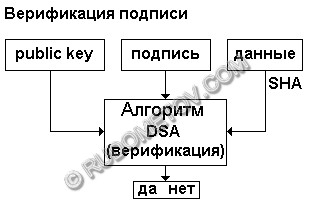
Fig. 6. The circuit of operations at signature verification
Operation with a key: reading from a file and conversion in PrivateKey.
The receiver allocates sequence the byte, representing an open key. It is necessary to receive the byte array (Byte [] encKey), for example, to read these data from a file in the array, and then to transform it to the object of class PublicKey.
For this purpose it is possible to take advantage of class KeyFactory which under the key specification can restore the object of class Key (PrivateKey and PublicKey are descendants of class Key). Thus, it is necessary to receive the so-called specification of a key. It can be received, being grounded on what standard used at key generation. In this case the key has been generated by means of the provider "SUN", therefore it satisfies to standard X.509.
Generation of the specification of a key (the package java.security.spec. * is necessary):
X509EncodedKeySpec pubKeySpec = new X509EncodedKeySpec (encKey);
Creation of the object of class KeyFactory corresponding to the digital signature and the provider "SUN".
KeyFactory keyFactory = KeyFactory.getInstance ("DSA", "SUN");
Reception of the object of class PublicKey
PublicKey pubKey = keyFactory.generatePublic (pubKeySpec);
Operation with the signature: reading from a file and Signature.
The signature also is necessary for translating in the byte array (Byte [] sigToVerify). Then it is necessary to create the object of type Signature, also as it became earlier.
Signature sig = Signature.getInstance ("SHA1withDSA", "SUN");
sig.initVerify (pubKey);
During reading it is necessary to apply a method update () sig object, to a similar case of creation of the signature.
Authentication (verification).
The closing stage of operation of the receiver is purely reception of the answer to a question on truthfulness of the signature and data. By means of a method verify () the object of class Signature it is possible to receive result boolean:
boolean verifies = sig.verify (sigToVerify);
Value will be true, if the given signature (sigToVerify) the real signature for the data, created with usage of an open key (pubKey).
It is necessary to mark, that the first stage linked to operation of the remailer, demands some time for generation of data necessary for sending. For the computer of a class of Intel of Pentium III with frequency generation time makes of 733 MHz approximately 10 seconds. By the way, time spent for verification 10 times less.
Except considered DSA, many other things are given also resources of cryptography protection, as RSA, DES and others. Their usage like presented DSA.
Source programs
Texts of already ready and working programs are more low presented. GSig.java signs data from a file data, generates an open key and the signature, writing them accordingly in files signature and publickey. And VSig.java reads data from files signature, publickey and data and displays the message on truthfulness of the signature (about correspondence of the signature to data).
It is necessary to mark, that the first stage (operation of the remailer) demands certain time for generation of data necessary for sending. For example, for the computer with the processor of Intel of Pentium III 733 MHz time demanded for generation 1024-bit keys and the signature of the small message, makes approximately 10 seconds. By the way, time spent for verification, 10 times less also makes less than second.
GSig.java
/* Generation DSA of the signature */
import java.io. *;
import java.security. *;
class GSig
{
//saving of the byte array with a file
public static void saveToFile (byte [] info, String filename)
{
try
{
FileOutputStream fos = new FileOutputStream (filename);
fos.write (info);
fos.close ();
}
catch (Exception e)
{
System.err.println ("Caught exception" + e.toString ());
}
}//saveToFile ()
public static void main (String args [])
{
try
{
/* Generation of keys */
KeyPairGenerator keyGen = KeyPairGenerator.getInstance ("DSA", "SUN");
SecureRandom random = SecureRandom.getInstance ("SHA1PRNG", "SUN");
keyGen.initialize (1024, random);
KeyPair pair = keyGen.generateKeyPair ();
PrivateKey priv = pair.getPrivate ();
PublicKey pub = pair.getPublic ();
/* Creation of the object of class Signature */
Signature dsa = Signature.getInstance ("SHA1withDSA", "SUN");
/* Initialization by a private key */
dsa.initSign (priv);
/* Data reading from a file "data". Method call update () */
FileInputStream fis = new FileInputStream ("data");
BufferedInputStream bufin = new BufferedInputStream (fis);
byte [] buffer = new byte [1024];
int len;
while (bufin.available ()! = 0)
{
len = bufin.read (buffer);
dsa.update (buffer, 0, len);
}
bufin.close ();
/* signature Generation */
byte [] realSig = dsa.sign ();
/* signature Saving in a file "signature" */
saveToFile (realSig, "signature");
/* Saving of an open key in a file "pubkey" */
byte [] key = pub.getEncoded ();
saveToFile (key, "pubkey");
}
catch (Exception e)
{
System.err.println ("Caught exception" + e.toString ());
}
}//main ()
}//class GSig
VSig.java
/* Verification DSA of the signature */
import java.io. *;
import java.security. *;
import java.security.spec. *;
class VSig
{
//reading from a file in the byte array
public static byte [] readFromFile (String fileName)
{
byte [] info;
try
{
FileInputStream fis = new FileInputStream (fileName);
info = new byte [fis.available ()];
fis.read (info);
fis.close ();
}
catch (Exception e)
{
System.err.println ("Caught exception" + e.toString ());
info = new byte [0];
}
return (info);
}//copyFromFile ()
public static void main (String args [])
{
try
{
/* Reception encoded public key from a file "pubkey" */
byte [] encKey = readFromFile ("pubkey");
/* Creation of the specification of a key */
X509EncodedKeySpec pubKeySpec = new X509EncodedKeySpec (encKey);
.* Creation of Лунафсещкн objects and ЗгидшсЛун*.
KeyFactory keyFactory = KeyFactory.getInstance ("DSA", "SUN");
PublicKey pubKey = keyFactory.generatePublic (pubKeySpec);
/* Reading of the signature from a file "signature" */
byte [] sigToVerify = readFromFile ("signature");
/* Creation of the object of class Signature and initialization by means of an open key */
Signature sig = Signature.getInstance ("SHA1withDSA", "SUN");
sig.initVerify (pubKey);
/* Data reading from a file "data" and method call update () */
FileInputStream datafis = new FileInputStream ("data");
BufferedInputStream bufin = new BufferedInputStream (datafis);
byte [] buffer = new byte [1024];
int len;
while (bufin.available ()! = 0)
{
len = bufin.read (buffer);
sig.update (buffer, 0, len);
}
bufin.close ();
/* Verification */
boolean verifies = sig.verify (sigToVerify);
System.out.println ("Signature verifies:" + verifies);
}
catch (Exception e)
{
System.err.println ("Caught exception" + e.toString ());
}
}//main ()
}//class VSig
Non-central cryptography in Perl
Popular enough Internet routed language Perl also has the built in resources of support of protection.
For an example we will consider usage of cryptography algorithm of enciphering RSA.
Algorithm RSA
The task which solves RSA, is classified information transmission so that to read its smog only a target.
The method essence consists in the following.
shifrovannogo messages are fulfilled by the potential receiver following operations:
· two big prime numbers (for example, 1024 bits, 308 signs) — p and q are generated ;
· their product n = pq is counted up ;
· the random number e which is mutually simple with number (p‑1) (q‑1) is selected, and also does not exceed it;
· d value such, that ed = 1 mod (p‑1) (q‑1) is counted up .
· the pair (n, e) becomes an open key (public key), and d — the closed key (private key).
The open key is published in open sources, for example, is transferred through e-mail.
shifrovannogo messages for operation it is necessary for remailer to fulfil following operations:
· to receive an open key;
· to create the message in numerical sort m, not exceeding n;
· to count up c = (me mod n value ;
· with also there is a ciphered message which goes to the creator of an open key.
The receiver of the encoded message calculates m = (cd) mod n and receives the message in the decrypted sort.
Firmness of algorithm RSA is provided thanks to that to the malefactor is necessary to receive number d which can be calculated, faktorizovav number n. However at present there are no the fast algorithms solving the task faktorizatsii of the big numbers.
The main methods of operation with RSA
In language Perl all cryptography is delivered through CPAN units. Implementation RSA is in package Crypt:: RSA.
Generation of 2048-bit keys:
$rsa = new Crypt:: RSA;
$public, $private) = $rsa-> keygen (Size => 2048)
The open key is published.
Data encoding (string $message) with usage of an open key:
my $c = $rsa-> encrypt (Message => $message, Key => $public);
As a result it turns out shifrovannoe the message $c which goes back to a target. The receiver uses for decryption earlier generated closed key $private:
$message = $rsa-> decrypt (Ciphertext => $c, Key => $private);
Except the presented strings of the source text in language Perl, it is necessary to mark and some additional features of a package.
For sending of the protected messages the information should be presented in the form of one or several numbers which values do not exceed n. Thus to each message there corresponds certain number and on the contrary. Resources of language Perl allow to mill the message on sequence of such numbers, and also further to joint them back in the text.
Unfortunately, in system RSA there is one important feature reducing a degree of security. If the malefactor can force to encode the remailer message already known to it p values and q can be counted up without faktorizatsii n. However with it it is possible to struggle successfully, overloading an original message "garbage" (padding). In due course standard PKCS has been developed for this operation #1. Crypt:: RSA realises not only PKCS #1, but also more modern OAEP which uses padding by default. At usage PKCS #1 it is necessary to handle appropriate parametre to the designer.
$rsa = new Crypt:: RSA (ES => ' PKCS1v15)
Example of usage of the digital signature
RSA
Authentication and integrity of the message usually dares by means of DSA algorithm. However there is a possibility to use and package Crypt:: RSA.
First of all it is necessary to generate keys. More often keys are already ready and are stored in a file under the password. For creation $private designer Crypt:: RSA:: Key:: Private () to which as parametres the filename and the password is handled uses.
$private = new Crypt:: RSA:: Key:: Private (
Filename => "keys/imja_fajla.private",
Password => ' the password '
);
The signature is carried out with the help $rsa-> sign (). Thus as parametres the message and the closed key appears.
$rsa = new Crypt:: RSA;
$signature = $rsa-> sign (Message => $message, Key => $private);
The message $message and the signature $signature go to a target which, using an open key, receives confirmation of authenticity of the signature:
$public = new Crypt:: RSA:: Key:: Public (
Filename => "keys/imja_fajla.public",);
$rsa-> verify (Message => $message,
Signature => $signature,
Key => $public)
|| die "the Signature counterfeit! \n";
DSA
DSA it is realised in package Crypt:: DSA. Usage DSA is similar to the RSA-signature, but there are also features.
Snachalo the DSA-key is generated:
use Crypt:: DSA;
$dsa = Crypt:: DSA-> new;
$key = $dsa-> keygen (Size => 512);
The signature is carried out by standard image:
$sig = $dsa-> sign (Message => $message, Key => $key);
To the receiver the message, the signature and an open key are besides dispatched. In process verification (the open key $pub_key) the signature uses either is accepted ($valid=true), or it is rejected ($valid=false).
$valid = $dsa-> verify (Signature => $sig,
$message,
Key => $pub_key);
In summary it is necessary to underline, that the realised algorithms of cryptography protection in packages for language Perl can widely use in the Internet oriented projects.
However it is necessary to mark, that programmers quite often meet a problem of a considerable quantity of every possible interfaces in various languages. In this connection there was a requirement for general-purpose interfaces.
General-purpose cryptography interfaces
Many corporations including the largest system integrators, applying cryptography protection in the application systems, have gone on path of implementation of general-purpose interfaces. Their tasks include allocation to the application of a wide set of possibilities on call of a certain set of cryptography tools. Such approach increases a system flexibility and provides independence of features of implementation of algorithms. Besides, reduces probability of appearance of the errors reducing a degree of security.
Originally many interfaces arose as intracorporate standards. Thus, have appeared CryptoAPI (Microsoft), Cryptoki (RSA Data Security), GCS-API (X/Open). The international organisation on standardization IETF (Internet Engineering Task Force) has tried to create the uniform general-purpose standard which has been named GSS-API. CpyptoAPI it is oriented to usage in OS of Windows NT while the others have no accurate limitations, but nevertheless use in OS Unix is more often.
In addition to the aforesaid it is necessary to mark, that software developers usually do not think of what algorithms of cryptography protection will use in their product. Only necessary interface of call of functions of the protection developed by the indirect manufacturer is provided.
Microsoft CryptoAPI
The order of interaction of applications with cryptography units of the operating system regulates the document which (MS CryptoAPI) is named as Microsoft Cryptographic Application Programming Interface. The functions described in it, are supported Windows 9x and Windows NT/2000/XP. In last OS of function CryptoAPI contain in crypt32.dll units and advapi32.dll. Actually these units do not realise cryptography algorithms, and access to other units named Cryptographic Service Providers (CSP). Simultaneously in the operating system it is possible to instal a little CSP. At the first call to CryptoAPI the application selects, with which CSP unit it will work depending on what cryptography algorithms are necessary for it (fig. 7). It is necessary to mark, that the system used in Java, on the organisation it is similar to the given.
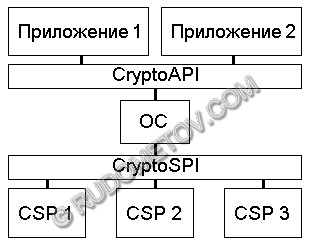
Fig. 7. CryptoAPI architecture circuit
CryptoAPI allows to cipher given to sign documents the digital signature and many other things. There are built in resources, for example, Microsoft Base Cryptographic Provider.
Thus, there is a possibility to use CryptoAPI in such programs of development, as Visual Studio. That is support of such languages, as Visual C ++, Visual Basic, Visual FoxPro and others is automatically carried out.
With development by the company of Microsoft of a language platform.NET, the majority of programming languages, including language C typing popularity #, cryptography methods of protection support.
Example of function of generation of keys can be CryptGenKey (). For enciphering and decoding are functions CryptEncrypt () and CryptDecrypt () and so on.
Usage kriptozashchity in other languages
If in language there are no built in resources of cryptography protection exists two possibilities.
First, it is possible to try to make all “from null”. Unfortunately, more often it is not given possible as it is linked to implementation of rather difficult algorithms.
The second way is usage of the object modules created with usage of compilers from different programming languages.
Let's accept, there is a number of languages on which demanded algorithms are already realised. Compilers from these languages provide reception of object codes which can be used at an application programming in other language. Naturally, it is not always easily realised. However such languages as, for example, Algol, the Fortran, PL1 thanks to similar syntax of language constructions and implementation of compilers, as a rule, are quite compatible in the given sense.
The operation example is presented on fig. 8.
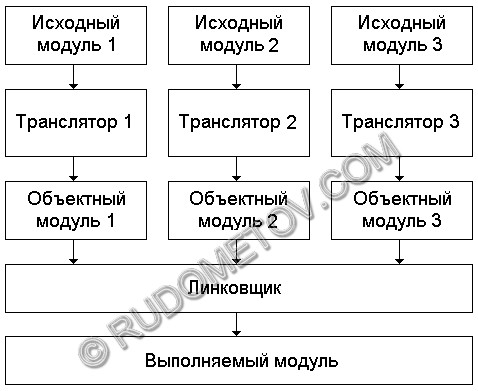
Fig. 8. An example of the circuit of multiplexing of the units created in different languages.
Considering possibility of application of the specified way, it is necessary to mark, that in case of the big difficulties of joining of the units created in different programming languages, as a rule, there is a possibility of usage for this purpose of the assembler. Thus appropriate structures of the assembler can be applied both to intermediate parametre passing, and for realisation of call of object modules.
The conclusion
In conclusion of the given browse it is possible to underline once again, that each described way of implementation of cryptography protection frames of the information possesses both advantages, and lacks. The choice is defined by tasks in view taking into account features of implementation, maintenance and financial possibilities. Thus it is necessary to consider the used hardware, a necessary degree of protection of the information etc.
In addition to it it is necessary to mark once again, that as practice shows, cryptography methods of protection really provide safety on rather high level. Undoubtedly, given direction will fast develop with the advent of new communication hardware-software resources. General-purpose cryptography interfaces try to develop the majority of the modern companies and to shield software developer from independent implementations of difficult algorithms. Both JDK security API and CryptoAPI, and the built in resources.NET give a rich kit of the enciphering, allowing to organise an own protection system of data. However it is necessary to mark, that on path of implementation of effective protection of the information there are still many technological difficulties. Nevertheless, appropriate hardware-software resources promptly develop. It allows to calculate for appearance of new solutions which, it is possible to hope, will be deprived existing while defects.
The literature
1. “Introduction in cryptography” / Under obshch. red. V.V.Jashchenko. — M.:МЦНМО, "CHeRo", 1998. — 272c.
2. A.Nikitin, “General-purpose cryptography interfaces”, information Protection, Konfident, N5, 1997.
3. M.Mogran, “Java 2. A manual of the implementator”, the Lane with English: Uch. Settlement — M: "Williams", 2000. — 720c.: silt.
4. Vipul Ved Prakash, Benjamin Trott, “Asymmetric Cryptography in Perl”, O'Reilly, 2001.
5. R.Coleridge, “The Cryptography API, or How to Keep a Secret”, MSDN, 1996.
6. D.Esposito, “Supporting CryptoAPI in Real-World Applications”, MSDN, 1997.
7. http://java.sun.com
8. S.K.Parmar, “An introduction to security”, Fred Cohen &Associates, 2000.
9. R.L/Rivest, A.Shamir and L.Adleman, “A method for obtaining digital signatures and public key cryptosystems”. Commun. ACM, vol.21, p. 120-126, 1978.
10. W.Diffie and M.E.Hellman, “New directions in cryptograpgy”, IEEE Trans. Inf. Theory, vol. IT 22, N6, p.644-654, Nov. 1976.
11. A.Menezes, P.van Oorschot, S.Vanstone, “Handbook of applied cryptography”, CRC Press, 1996.
Article is published in log the Computer the Press (http://www.compress.ru/).
 English
English Russian
Russian German
German